Zero Trust identity built on the best compliance standards in the industry.
On your journey towards Zero Trust, identity is the cornerstone of security. Whether it’s designing the necessary processes, ensuring a proper lifecycle, securing access and authorisation, or helping automate these elements, we can help you address these challenges:
Implementation of Zero Trust and identity management introduces a complex infrastructure and operational workflow, posing challenges in designing and integrating the necessary controls and policies.
Organisations struggle to find and hire cyber security professionals with the expertise needed to implement and manage Zero Trust architecture and identity management systems.
Limited resources and budget constraints can hinder organisations from making the necessary investments in technology, infrastructure, and personnel to establish and maintain a robust Zero Trust environment.
Strengthen your defences with versatile solutions to cater for dynamic environments and applications existing in the cloud or on-premise. Our identity experts take the complexity out of your identity and access lifecycle.
ITC’s cyber advisory services provide you with access to expert cyber advisors who will guide your business in defining and maintaining industry-leading cyber security standards.
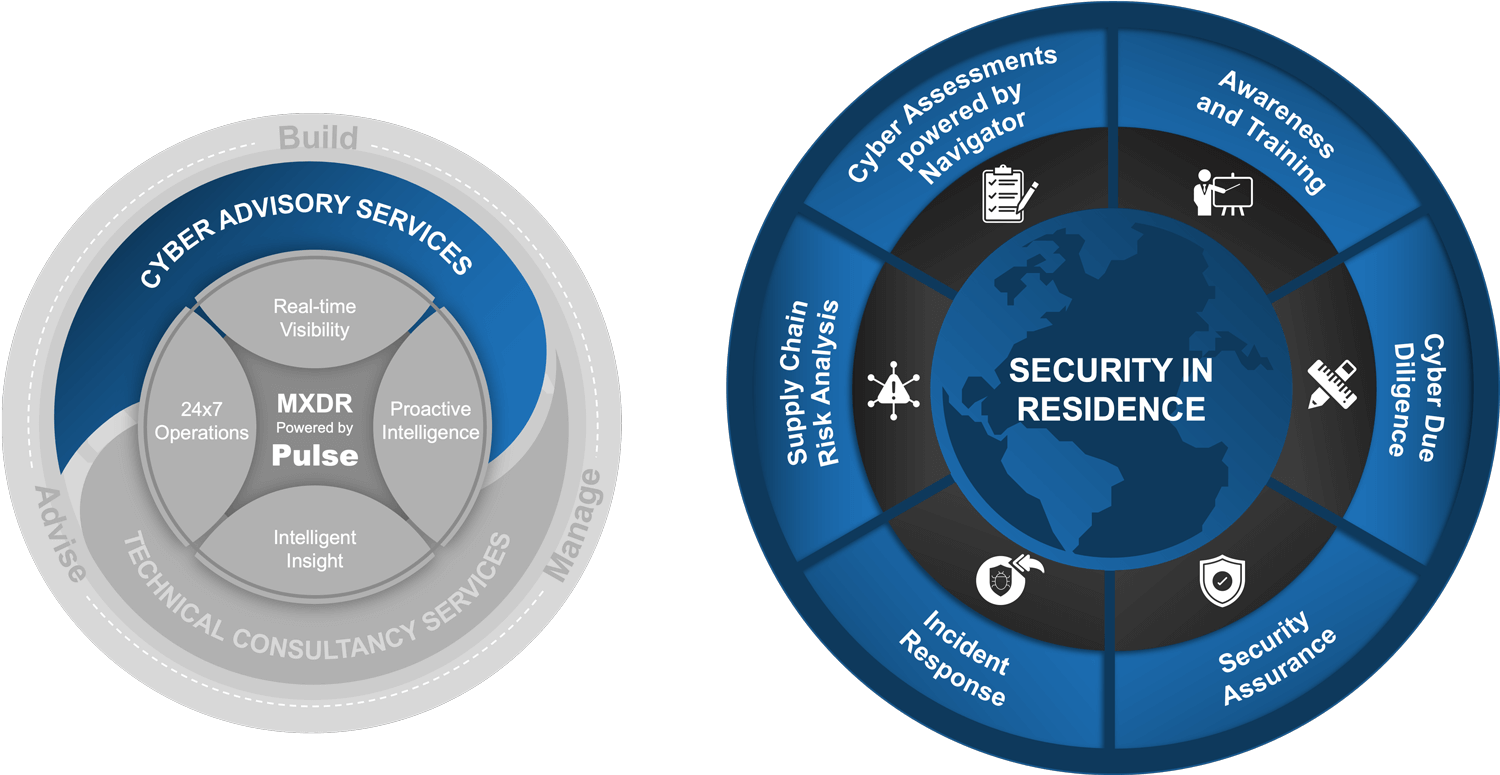
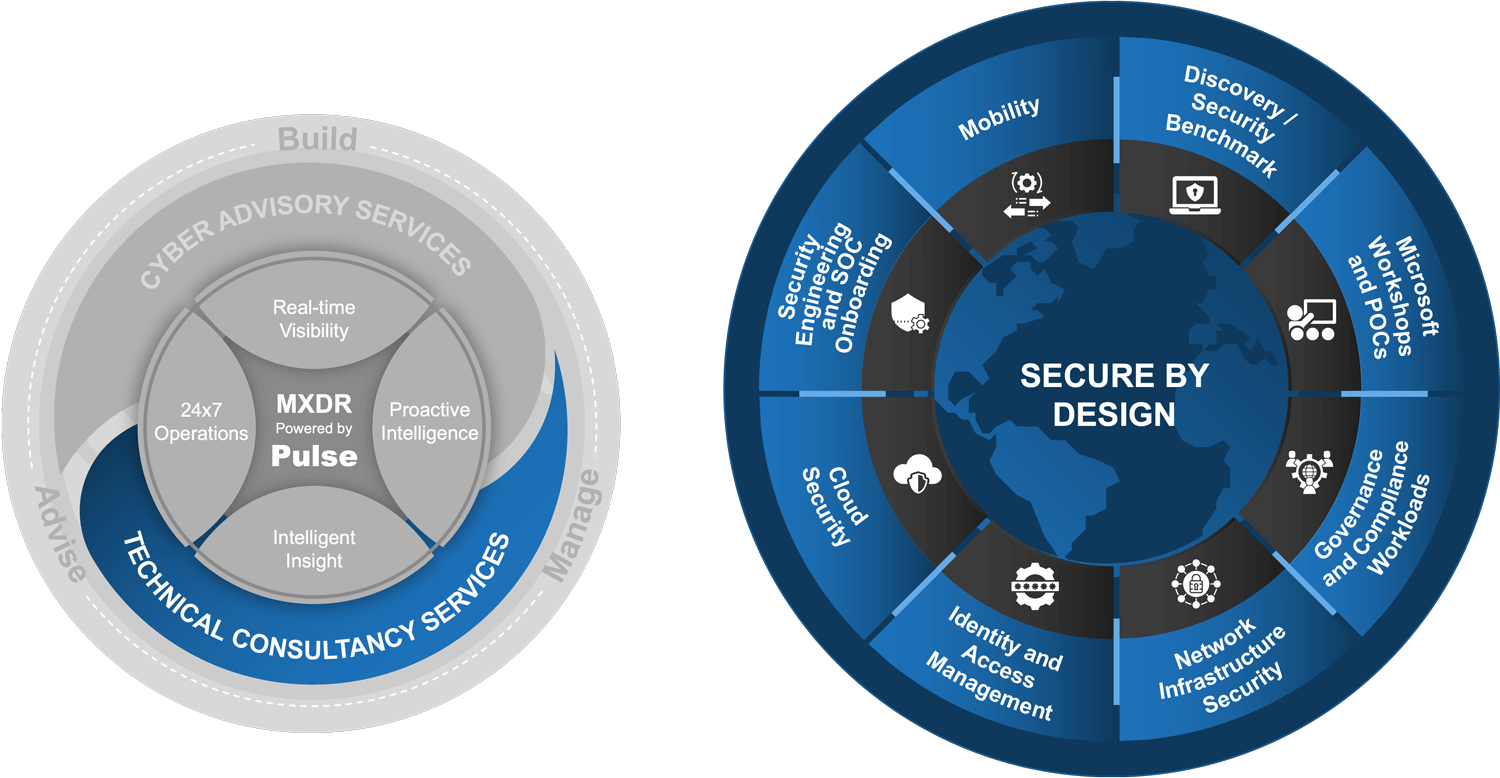
ITC’s technical consultancy services empower your business with access to cyber consultants and Microsoft experts who offer design, build and delivery best practices with expertise in the areas of security, cloud and identity.
Work with you to understand your business needs – alleviating the burden of analysing and investigating security alerts 24×7.
Tailor your solution based on our assessment — built for today with flexibility to scale for the future.
Provide proactive intelligent insight on the steps you need to take to make cyber resilience your competitive advantage.
Build and run your cyber solution so that you can focus on what matters: your business.