Priority: Critical
Summary
Enterprise networking vendor F5 Networks has released details of multiple critical remote code execution (RCE) vulnerabilities affecting most versions of BIG-IP and BIG-IQ. F5 is urging all customers to update their deployments as soon as possible. 1
The four most critical vulnerabilities include a pre-authentication RCE vulnerability, which would allow an unauthenticated remote attacker to execute arbitrary commands on vulnerable devices:
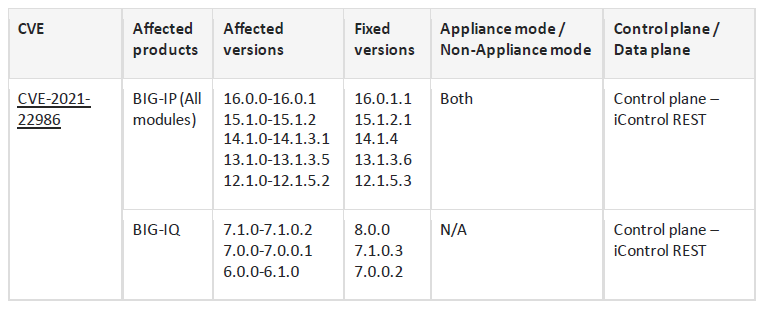
- CVE-2021-22986 – iControl REST unauthenticated RCE vulnerability. CVSSv3 score: 9.8 (critical).
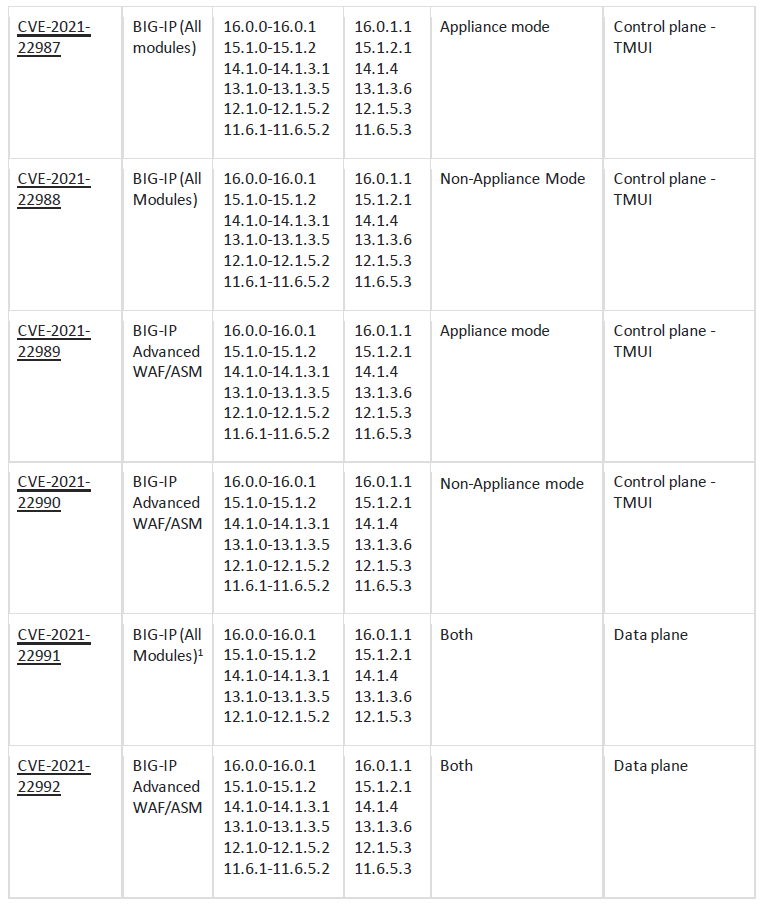
- CVE-2021-22987 – Appliance Mode TMUI authenticated RCE vulnerability. CVSSv3 score: 9.9 (critical).
- CVE-2021-22991 – TMM buffer overflow vulnerability. CVSSv3 score: 9.0 (critical).
- CVE-2021-22992 – Advanced WAF/ASM buffer overflow vulnerability. CVSSv3 score: 9.0 (critical).
In addition, F5 also identified three other related vulnerabilities; two high severity and one medium (CVE-2021-22988, CVE-2021-22989, and CVE-2021-22990, respectively). 2
No information has been given about whether any public exploit for these vulnerabilities is known. However, compromised networking devices give attackers a great deal of access into their targets’ environments, so these vulnerabilities are likely to attract a lot of attention and it can be assumed that exploits will be developed quickly.
Detect
Users of BIG-IP and BIG-IQ products should refer to the following table of affected products to see if the versions in their environments are vulnerable:
React
Users with known vulnerable versions – including users leveraging public cloud marketplaces (AWS, Azure, GCP, and Alibaba) to deploy BIG-IP Virtual Edition – should patch to the appropriate fixed version. If no fixed version is listed for your current software branch, F5 recommends upgrading to a branch that contains the fix. F5 has provided full details, including any relevant mitigations for where patching is not immediately possible, in articles for each of the vulnerabilities:
- CVE-2021-22986 – K03009991: https://support.f5.com/csp/article/K03009991
- CVE-2021-22987 – K18132488: https://support.f5.com/csp/article/K18132488
- CVE-2021-22988 – K70031188: https://support.f5.com/csp/article/K70031188
- CVE-2021-22989 – K56142644: https://support.f5.com/csp/article/K56142644
- CVE-2021-22990 – K45056101: https://support.f5.com/csp/article/K45056101
- CVE-2021-22991 – K56715231: https://support.f5.com/csp/article/K56715231
- CVE-2021-22992 – K52510511: https://support.f5.com/csp/article/K52510511
ITC customers with managed networking services using F5 devices have already been contacted by our Operations Centre, informed of the patching requirement and appropriate arrangements are being made through respective change control processes.
Sources:
[1] https://www.f5.com/company/blog/big-ip-and-big-iq-vulnerabilities-protecting-your-organization




