Priority: High
Executive Summary: Researchers at Check Point have uncovered a number of vulnerabilities in three Remote Desktop Protocol (RDP) Clients: Microsoft’s RDP client, rdesktop, and FreeRDP, which can be exploited by a malicious server when the client connects to it over RDP. This would allow an attacker who had compromised a user’s device to move laterally to an administrative device when the administrator RDP’d to the infected machine.
The vulnerability in Microsoft’s RDP client exists in the shared clipboard between the client and the server. When bidirectional copy and paste functionality is enabled over these RDP connections, the user may copy files between the client and the server. If a user is connected over an RDP session with this feature enabled, then an infected server could report to the client that it had copied a file from the server. The server will then send this file even if the user has not copied anything from the server’s environment.
The RDP client is furthermore susceptible to a path-traversal attack in this process. This means that the attacker can drop arbitrary files into arbitrary locations when a user attempts to paste anything during such an RDP session, ‘without any notification to the user’. An attacker can therefore place a malicious executable
file in the user’s startup folder, which will execute after the user next restarts their device.
This vulnerability does not affect rdesktop and FreeRDP, as files cannot be transferred through these RDP
clients.
rdesktop and FreeRDP were discovered to be susceptible to numerous exploits due to lack of input checking, allowing integer overflow and buffer overflow attacks, consequently allowing for remote code execution. These issues have been addressed in the most recent versions of the two open-source RDP clients.
Whilst rdesktop and FreeRDP have released updated versions of their software, Microsoft have no current plans to address the path traversal vulnerability in their product, which is integral to the attack becoming a real threat. Disabling bidirectional copy and paste functionality is therefore the only way to completely protect against this issue.
Detect:
rdesktop versions v.1.8.3 and earlier are vulnerable, as are FreeRDP versions 2.0.0-rc3 and prior. (See Appendix A and Appendix B for a list of vulnerabilities for rdesktop and FreeRDP respectively.) Administrators will need to investigate which versions of these are installed on devices which host RDP servers.
All versions of Microsoft’s RDP client with bidirectional copy and paste functionality enabled are vulnerable.
Affected Products:
Microsoft’s RDP client is widely used for establishing RDP sessions between Windows machines.
Prevent: rdesktop can be updated to version v.1.8.4, and FreeRDP can be updated to version 2.0.0-rc4 to remediate these vulnerabilities.
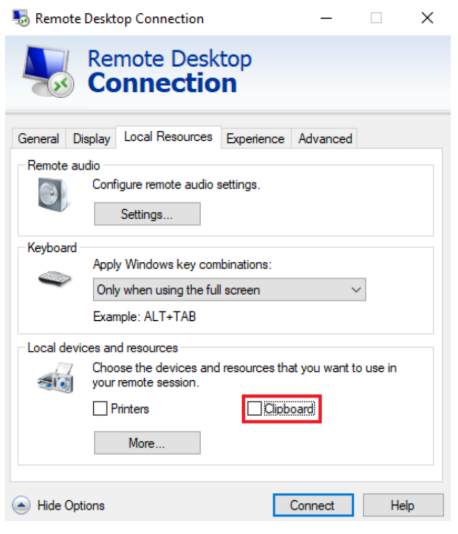
The bidirectional clipboard can be disabled from the host when establishing the RDP connection simply be deselecting the ‘Clipboard’ option under ‘Local Resources’ before connecting, as shown below:
React: Ensure that any devices running rdesktop or FreeRDP have updated these to the latest version.
Companies may wish to deter users from enabling a bidirectional keyboard when establishing RDP sessions
between Windows machines until Microsoft addresses the vulnerability in their client.
Sources:
[1] https://research.checkpoint.com/reverse-rdp-attack-code-execution-on-rdp-clients/


